
Enhancing Data Security: Exploring Advanced Storage Solutions
Storage Data Security refers to protective digital privacy measures that are applied to prevent unauthorized access to databases, websites, and computers. It serves to safeguard your important data from corruption, compromise or loss, ensuring business continuity, minimizing downtime, and providing a seamless flow of information.
Introduction to Storage Data Security
Storage data security refers to the protective digital privacy measures that are applied to prevent unauthorized access to databases, websites, and computers. This involves various tactics and methods to protect data from corruption, compromise, or loss. Read more
Importance of Storage Data Security
In the modern digital age, data is a valuable resource. It's imperative for businesses and individuals to protect their sensitive data. Storage data security helps to keep personal and business information safe from cyber threats like data breaches, ransomware attacks, and other forms of cybercrime. Read more
Types of Storage Data Security
There are different types of storage data security, including disk encryption, backup solutions, and cloud storage security. Each type has its own unique set of security measures and protocols designed to protect stored data. Read more
Disk Encryption
Disk encryption is a technology that protects information by converting it into unreadable code. Only with the correct password or decryption key can the data be accessed. Examples of disk encryption software include BitLocker and FileVault. Read more

Backup Solutions
Backup solutions are essential for preventing data loss. This involves creating a copy of data that can be recovered in case the original data is lost or damaged. Popular backup solutions include services like Acronis True Image and Carbonite. Read more
Cloud Storage Security
Cloud storage security involves protecting data stored online in the cloud against theft, leakage, and deletion. Providers of cloud storage services like Google Drive, Dropbox, and Microsoft OneDrive implement strong security measures including encryption and strong user authentication. Read more
Implementing Storage Data Security
Implementing storage data security involves a combination of good practices, such as regularly updating and patching systems, using strong and unique passwords, and employing the use of security software like antivirus and anti-malware programs. Read more
Storage Data Security and Compliance
Many industries have compliance standards that outline how data must be protected. These include standards like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Compliance with these standards is essential for legal operations and customer trust. Read more

Future of Storage Data Security
As cyber threats continue to evolve, so too will the methods for protecting stored data. Future advancements may include the use of artificial intelligence and machine learning to detect and neutralize threats. Read more
Conclusion on Storage Data Security
In conclusion, storage data security is an essential aspect of any modern business or individual's digital life. It offers protection against a multitude of cyber threats, and helps maintain trust, integrity, and compliance in a digital world. Read more
Read more
 Data Storage Security - How Secure Is Your Data? | Hypertec SP
Data Storage Security - How Secure Is Your Data? | Hypertec SP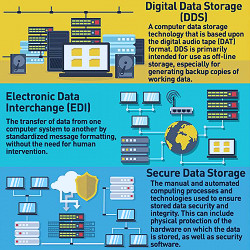 Data Storage Security - How Secure Is Your Data? | Hypertec SP
Data Storage Security - How Secure Is Your Data? | Hypertec SP 6 Essential Data Storage Security Best Practices to Know
6 Essential Data Storage Security Best Practices to Know Cloud Storage Security: How to Secure Your Data in the Cloud
Cloud Storage Security: How to Secure Your Data in the Cloud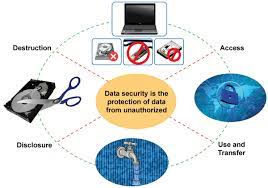 FAU | Data Security Storage
FAU | Data Security Storage 6 Cloud Storage Security Best Practices | Sanity Solutions INC
6 Cloud Storage Security Best Practices | Sanity Solutions INC Factors Behind Data Storage Security: Is Your Business Vulnerable?
Factors Behind Data Storage Security: Is Your Business Vulnerable? How Secure is Cloud Storage? | Terranova Security
How Secure is Cloud Storage? | Terranova Security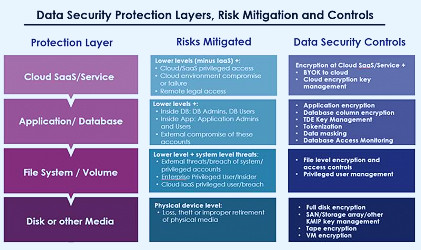 Data Storage Security - How Secure Is Your Data? | Hypertec SP
Data Storage Security - How Secure Is Your Data? | Hypertec SP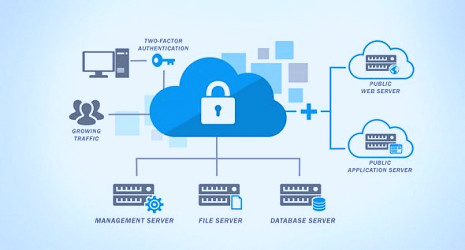 Cloud Storage Security Best Practices | GlobalDots
Cloud Storage Security Best Practices | GlobalDots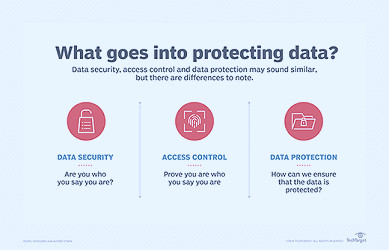 What is Storage Security? How to Secure Company Data
What is Storage Security? How to Secure Company Data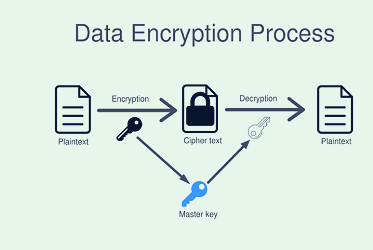 Ensure Data Security in Cloud Computing | Cloud Managed Services
Ensure Data Security in Cloud Computing | Cloud Managed Services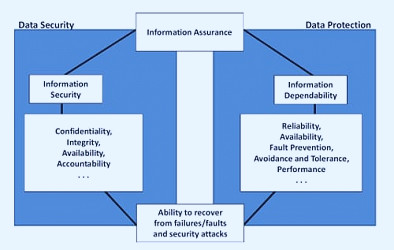 What Is Data Storage Security? | A Guide to Data Security | ESF
What Is Data Storage Security? | A Guide to Data Security | ESF How does data security and privacy law work for data storage Sigma Data Systems
How does data security and privacy law work for data storage Sigma Data Systems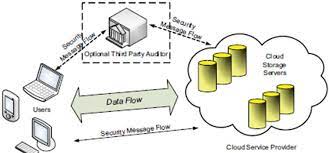 Ensuring data storage security in distributed cloud computing. | Download Scientific Diagram
Ensuring data storage security in distributed cloud computing. | Download Scientific Diagram Security Best Practices to Protect Self-Storage From Cyber Attack | Inside Self-Storage
Security Best Practices to Protect Self-Storage From Cyber Attack | Inside Self-Storage Are Employees' Use of Cloud Storage a Security Risk? - Rick's Cloud
Are Employees' Use of Cloud Storage a Security Risk? - Rick's Cloud The Truth Behind Cloud Storage Security Risks | WHOA.com
The Truth Behind Cloud Storage Security Risks | WHOA.com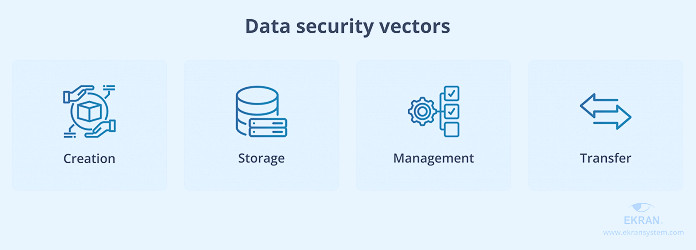 Data Security Best Practices: 10 Methods to Protect Your Data | Ekran System
Data Security Best Practices: 10 Methods to Protect Your Data | Ekran System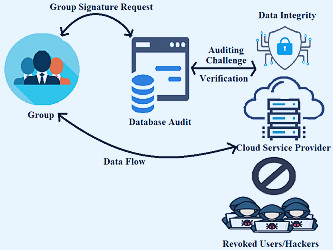 Electronics | Free Full-Text | Enhanced Cloud Storage Encryption Standard for Security in Distributed Environments
Electronics | Free Full-Text | Enhanced Cloud Storage Encryption Standard for Security in Distributed Environments 

