Unlocking Business Efficiency: A Comprehensive Review of MDM Software
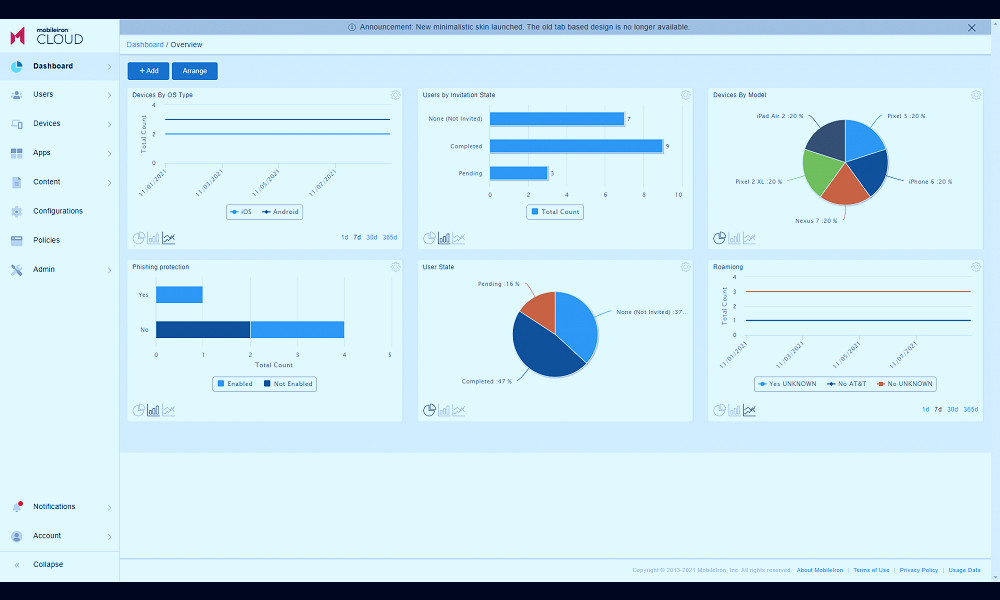
MDM software, also known as Mobile Device Management software, is a security platform designed to monitor, manage, and secure employees' mobile devices that are deployed across multiple operating systems. It allows companies to enforce security policies, manage apps, and protect their network from potential threats, while ensuring seamless communication and productivity among teams.
Understanding MDM
MDM, or Mobile Device Management, is a type of security software used by an IT department to monitor, manage, and secure employees' mobile devices that are deployed across multiple mobile service providers and across multiple mobile operating systems used in the organization. Read more
Key Features of MDM
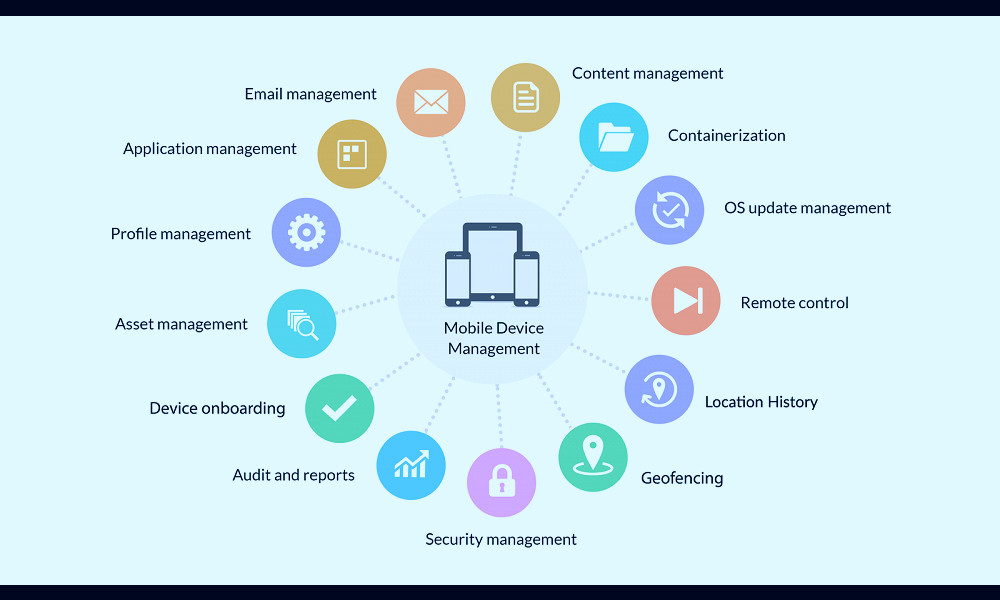
The essential features of MDM software include application management, file synchronization and sharing, data security tools, and support for either a corporate-owned or personally owned device. Read more
The Importance of MDM
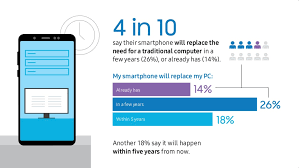
With the increasing trend of BYOD (Bring Your Own Device) in corporate culture, MDM helps to prevent corporate data leakage. It ensures safe and secure access to corporate documents on employees' devices. Read more
Popular MDM Brands
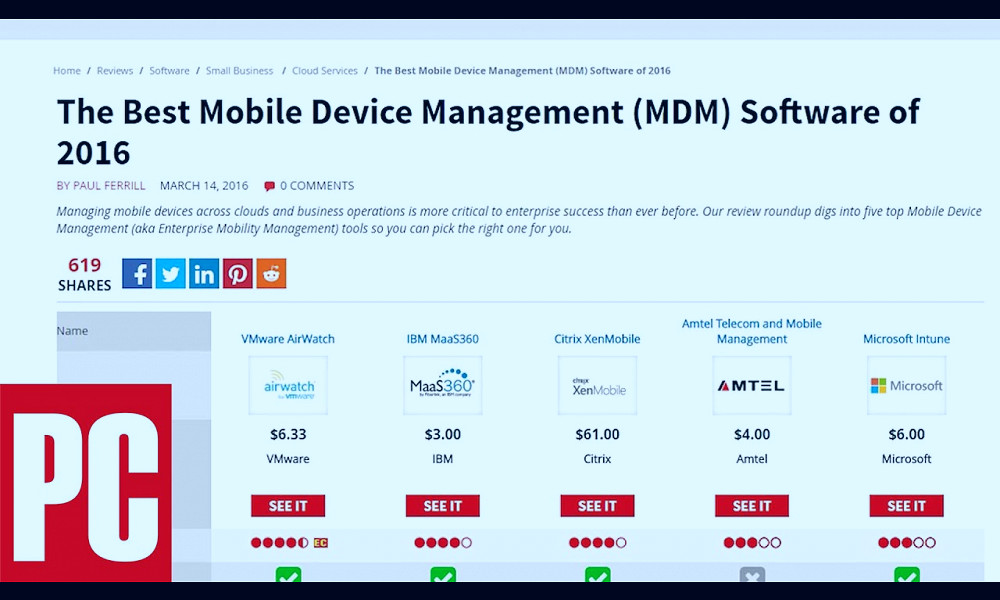
Some of the leading MDM brands are MobileIron, AirWatch, IBM, Citrix, and Microsoft. These brands offer comprehensive MDM solutions that cater to a variety of business needs. Read more

MDM and Cloud
Modern MDM solutions offer cloud-based deployment options. Cloud-based MDM, or Mobile Device Management as a Service (MDMaaS), provides scalability, disaster recovery, and high availability. Read more
Implementation of MDM
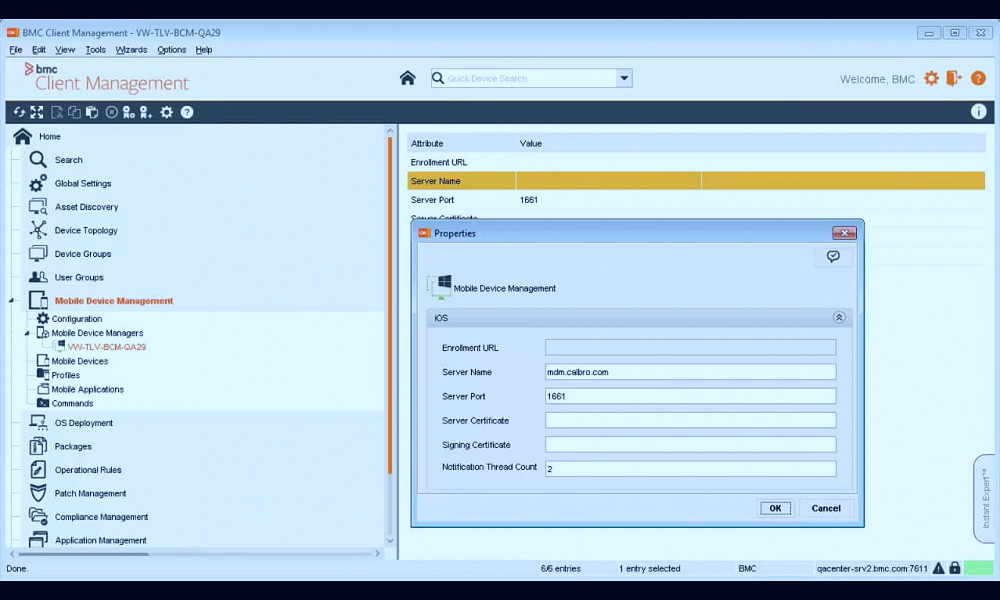
The implementation of MDM requires careful planning. It involves device enrollment, device authentication, device configuration, policy assignment, and continuous monitoring and management. Read more
Device Enrollment in MDM
Device Enrollment is the first step in implementing MDM. It involves adding the device to the MDM server, either manually or automatically. Read more
MDM and Data Security
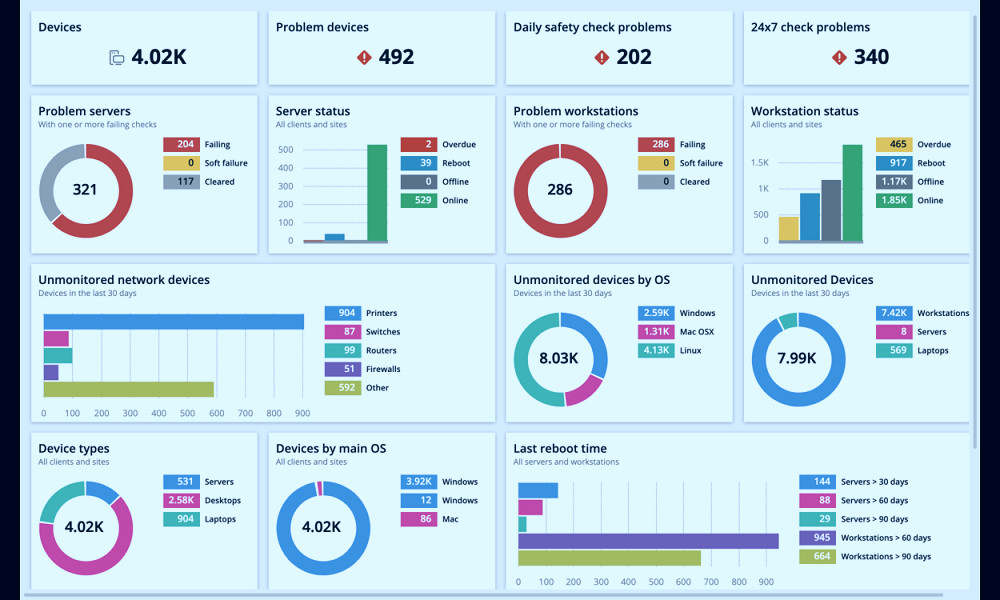
MDM offers data encryption, remote wipe, and anti-malware features to protect corporate data. It also provides secure access to corporate email and secure web browsing. Read more

MDM and Compliance
MDM software helps organizations comply with data protection regulations such as GDPR, HIPAA, and SOX. It provides audit logs, compliance reporting, and data loss prevention (DLP) capabilities. Read more
The Future of MDM
The future of MDM is likely to be driven by developments in areas such as machine learning, artificial intelligence, and the Internet of Things. This may result in more sophisticated, predictive, and proactive MDM solutions. Read more
Read more
 What is MDM? | MDM Software & Solutions
What is MDM? | MDM Software & Solutions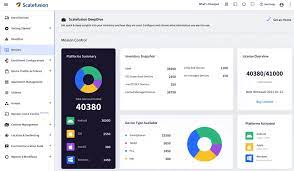 15 Best MDM Solutions 2023 (Paid & Free)
15 Best MDM Solutions 2023 (Paid & Free)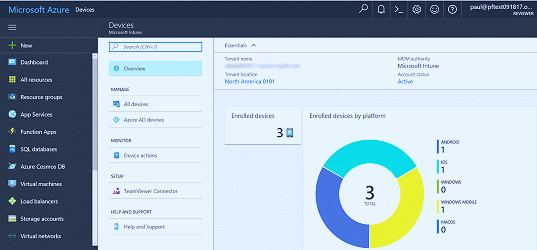 The Best Mobile Device Management (MDM) Solutions | PCMag
The Best Mobile Device Management (MDM) Solutions | PCMag![10 Best MDM Software Solutions in 2023 [SELECTIVE ONLY]](/static/mdm software/4.thumb.jpg) 10 Best MDM Software Solutions in 2023 [SELECTIVE ONLY]
10 Best MDM Software Solutions in 2023 [SELECTIVE ONLY]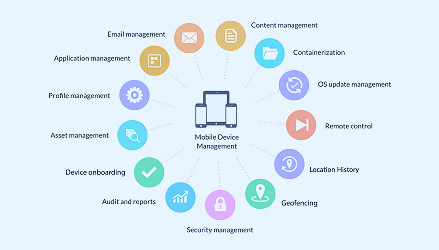 Mobile Device Management for Enterprises | MDM defined
Mobile Device Management for Enterprises | MDM defined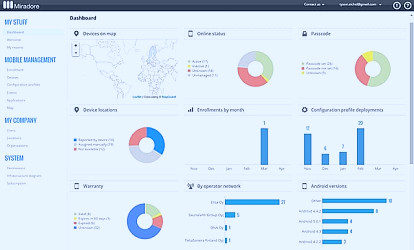 15 Best MDM Solutions 2023 (Paid & Free)
15 Best MDM Solutions 2023 (Paid & Free) What is Mobile Device Management (MDM)? Benefits and Device Management Software Comparison
What is Mobile Device Management (MDM)? Benefits and Device Management Software Comparison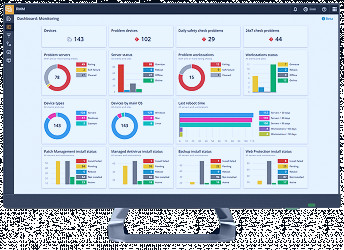 8 Best MDM Software Solutions - DNSstuff
8 Best MDM Software Solutions - DNSstuff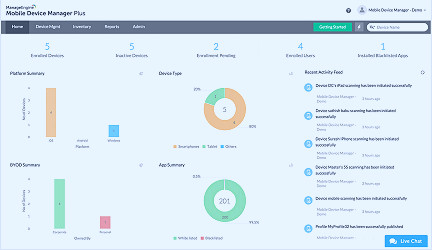 MDM Cloud | Mobile Device Management (MDM) Software - Zoho MDM
MDM Cloud | Mobile Device Management (MDM) Software - Zoho MDM![Everyone Regrets Not Understanding MDM Sooner [2023]](/static/mdm software/10.thumb.jpg) Everyone Regrets Not Understanding MDM Sooner [2023]
Everyone Regrets Not Understanding MDM Sooner [2023] What is MDM? | MDM Software & Solutions
What is MDM? | MDM Software & Solutions The Best Mobile Device Management (MDM) Solutions | PCMag
The Best Mobile Device Management (MDM) Solutions | PCMag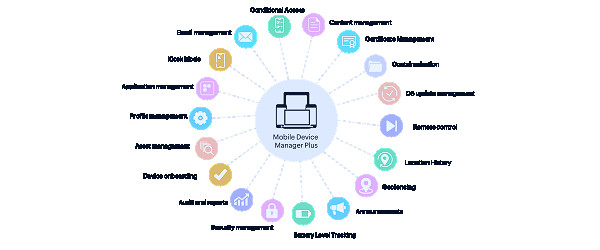 Android MDM | Android Device Management Software
Android MDM | Android Device Management Software The Best Mobile Device Management (MDM) Software of 2016 - YouTube
The Best Mobile Device Management (MDM) Software of 2016 - YouTube Top 5 MDM Software for 2022 - Best Mobile Device Management Tools
Top 5 MDM Software for 2022 - Best Mobile Device Management Tools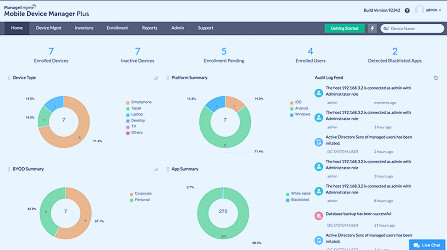 Best Mobile Device Management Software - 2023 Reviews & Pricing
Best Mobile Device Management Software - 2023 Reviews & Pricing The Top 10 Mobile Device Management (MDM) Solutions | Expert Insights
The Top 10 Mobile Device Management (MDM) Solutions | Expert Insights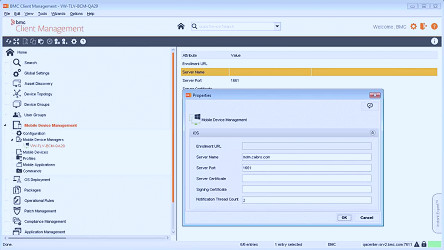 What is Mobile Device Management (MDM)? - Track-It!
What is Mobile Device Management (MDM)? - Track-It! 15 Best MDM Solutions 2023 (Paid & Free)
15 Best MDM Solutions 2023 (Paid & Free)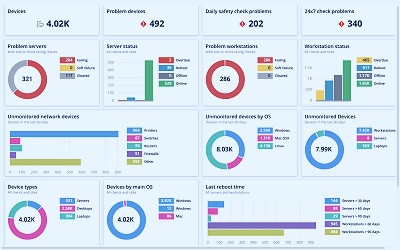 ADM Software Solutions for MSP Enterprises - N-able
ADM Software Solutions for MSP Enterprises - N-able 
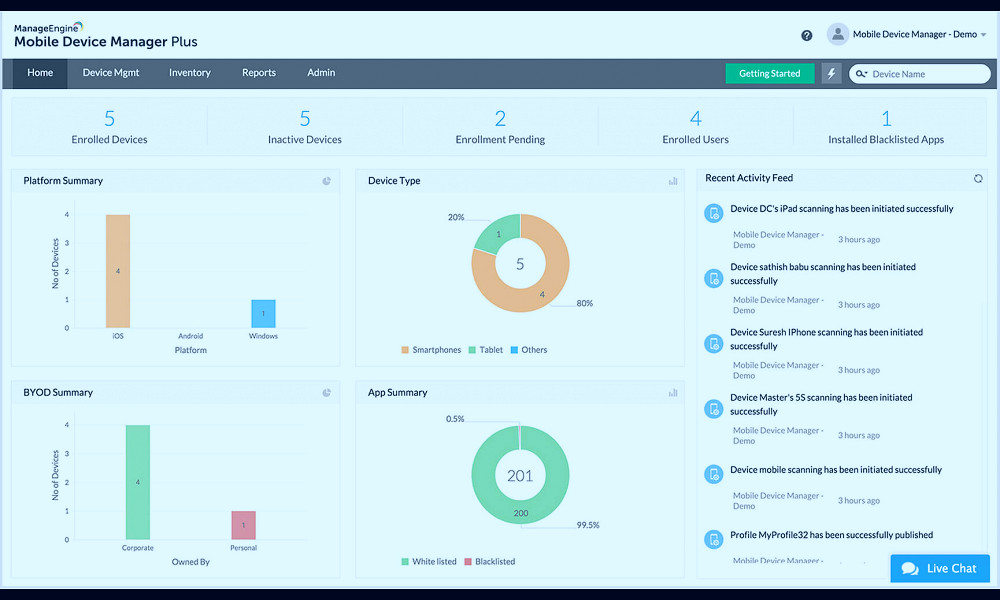
![Everyone Regrets Not Understanding MDM Sooner [2023]](/img/mdm-software.big.10.jpg)