Enhancing Your Online Safety: An In-depth Look at Cloud Web Security
Cloud Web Security is an advanced cybersecurity solution that protects your online data and activities. It monitors and controls web traffic in real-time, using cloud-based technology to detect and block threats such as malware, phishing, and data breaches. This solution is ideal for businesses and individuals who want to secure their online operations without compromising on speed or accessibility.
Understanding Cloud Web Security
Cloud Web Security, also often referred to as Cloud-Based Web Security, is a service that provides protection for a business's online presence. It is delivered over the internet and offers comprehensive security measures that help to protect the business's web use. Read more
Importance of Cloud Web Security
The security of web-based applications is critical in today's digital age. With increasing threats of cyber-attacks and data breaches, businesses need robust security measures in place. Cloud Web Security provides an extra layer of protection, safeguarding sensitive data and applications from potential threats. Read more
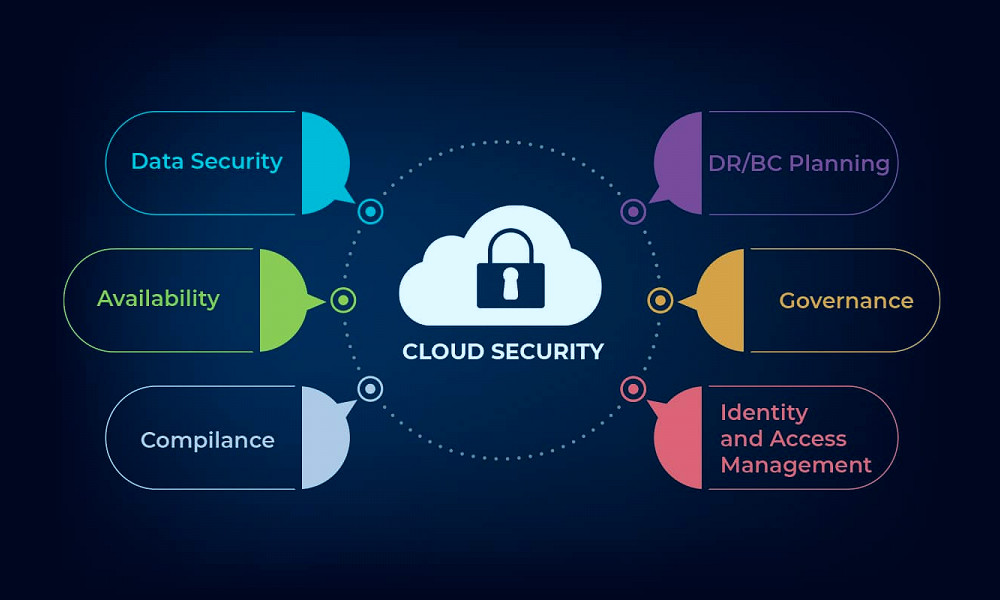
Key Features of Cloud Web Security
Cloud Web Security offers several features like real-time threat intelligence, secure web gateways, data loss prevention, and sandboxing. These features work together to provide a secure environment for businesses to operate online. Read more
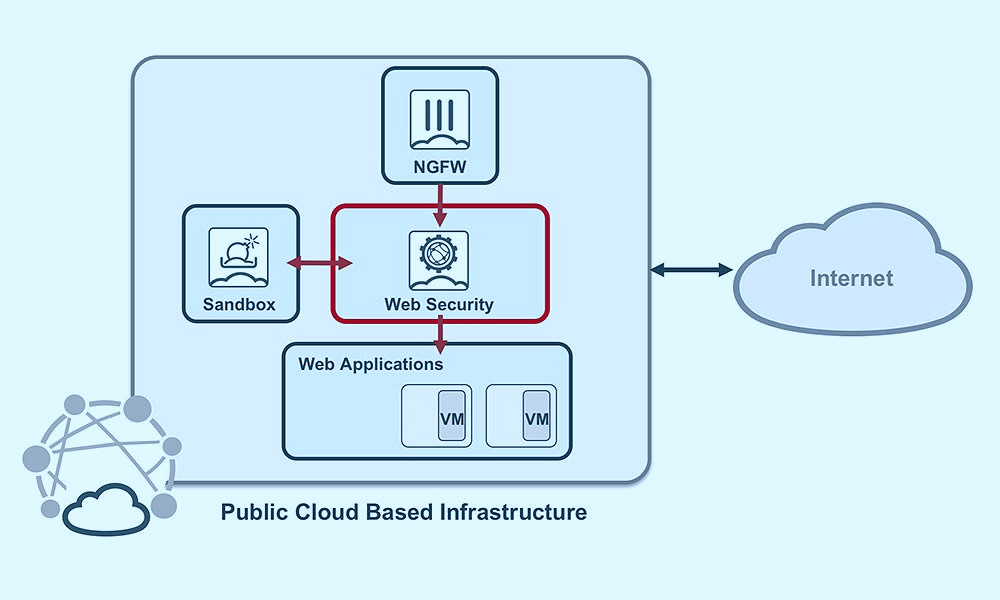
How Cloud Web Security Works
Cloud Web Security operates by routing a company's web traffic through a cloud-based security solution where it is inspected for potential threats or malicious content. Any suspicious activity is blocked, ensuring the safety of the organization's network. Read more

The Role of Encryption in Cloud Web Security
Encryption is a key component of Cloud Web Security. It ensures that data transmitted over the internet is unreadable to anyone who might intercept it, providing an additional layer of security. Read more
The Flexibility of Cloud Web Security
One of the major benefits of Cloud Web Security is its flexibility. As it's a cloud-based solution, it can be rapidly scaled up or down to meet the changing needs of a business. This makes it a cost-effective security solution for businesses of all sizes. Read more
The Impact of Cloud Web Security on Business Performance
By securing a company's online presence, Cloud Web Security can improve business performance. It allows businesses to operate online without the risk of cyber threats, leading to increased trust from customers and potentially higher sales. Read more
Cloud Web Security and Compliance
Cloud Web Security solutions often come with built-in compliance features. These help businesses meet various regulatory requirements related to data protection and privacy, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Read more

The Future of Cloud Web Security
The increasing reliance on web-based applications and the cloud means that Cloud Web Security will continue to be critical. Future developments in this field are likely to involve the use of artificial intelligence and machine learning to provide even more robust security solutions. Read more
Choosing a Cloud Web Security Provider
When choosing a Cloud Web Security provider, it's important to consider factors like the provider's reputation, the features offered, the level of customer support, and cost. Look for a provider that offers a comprehensive, flexible, and scalable solution to meet your business's unique needs. Read more
Read more
 Cloud Web Security | VMware
Cloud Web Security | VMware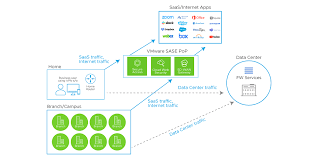 Cloud Web Security | VMware
Cloud Web Security | VMware What is cloud security?
What is cloud security? Cloud Security: Key Concepts, Threats, and Solutions - Security News
Cloud Security: Key Concepts, Threats, and Solutions - Security News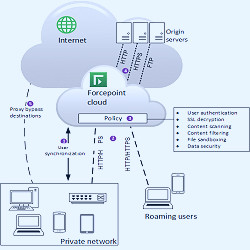 How Forcepoint Web Security Cloud works
How Forcepoint Web Security Cloud works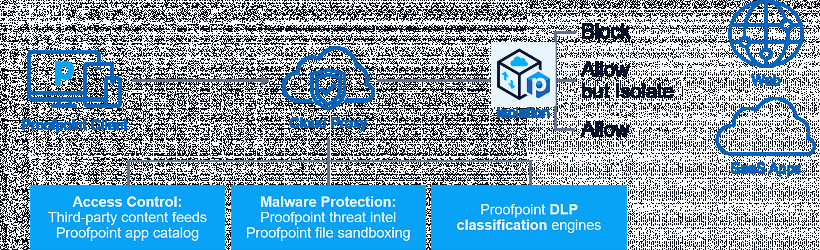 Cloud Web Security Services - Web Threat Protection | Proofpoint US
Cloud Web Security Services - Web Threat Protection | Proofpoint US cloud web security
cloud web security VMware Cloud Web Security: Always-On Security Connecting Distributed Workforces to Web Applications - VMware SASE and Edge
VMware Cloud Web Security: Always-On Security Connecting Distributed Workforces to Web Applications - VMware SASE and Edge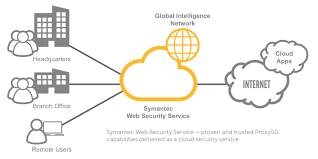 CST | Symantec Web Security Service (WSS)
CST | Symantec Web Security Service (WSS)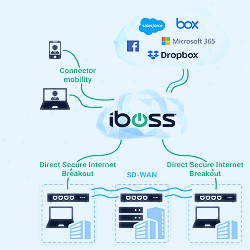 Cloud Based Branch Office Web Security - iboss
Cloud Based Branch Office Web Security - iboss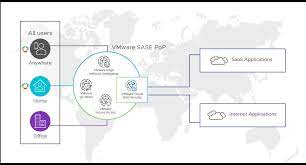 Announcing General Availability of VMware Cloud Web Security - VMware SASE and Edge
Announcing General Availability of VMware Cloud Web Security - VMware SASE and Edge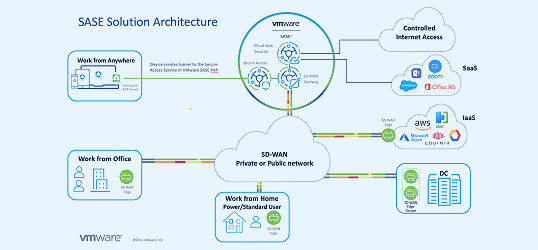 Latest News – SD-WAN with Secure Access & Cloud Web Security - SASE
Latest News – SD-WAN with Secure Access & Cloud Web Security - SASE How to mitigate cloud security threats | Industrial Cybersecurity Pulse | Industrial Cybersecurity Pulse
How to mitigate cloud security threats | Industrial Cybersecurity Pulse | Industrial Cybersecurity Pulse The Top 10 Web Security Solutions | Expert Insights
The Top 10 Web Security Solutions | Expert Insights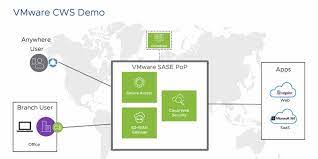 Cloud Web Security | VMware | ES
Cloud Web Security | VMware | ES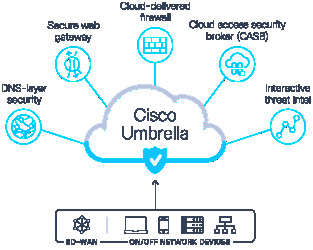 The Best Secure Web Gateway Business Solution - Cisco Umbrella
The Best Secure Web Gateway Business Solution - Cisco Umbrella Cybersecurity Strategy | Cloud4C Managed Security Services
Cybersecurity Strategy | Cloud4C Managed Security Services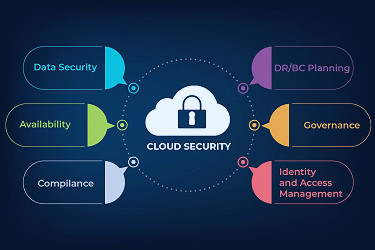 Cloud security - A Detailed guide - EES Corporation
Cloud security - A Detailed guide - EES Corporation Integrate With Google Cloud Web Security Scanner | Mindflow
Integrate With Google Cloud Web Security Scanner | Mindflow Cloud Security – Amazon Web Services (AWS)
Cloud Security – Amazon Web Services (AWS)