Exploring the Best Vulnerability Management Tools for Cybersecurity
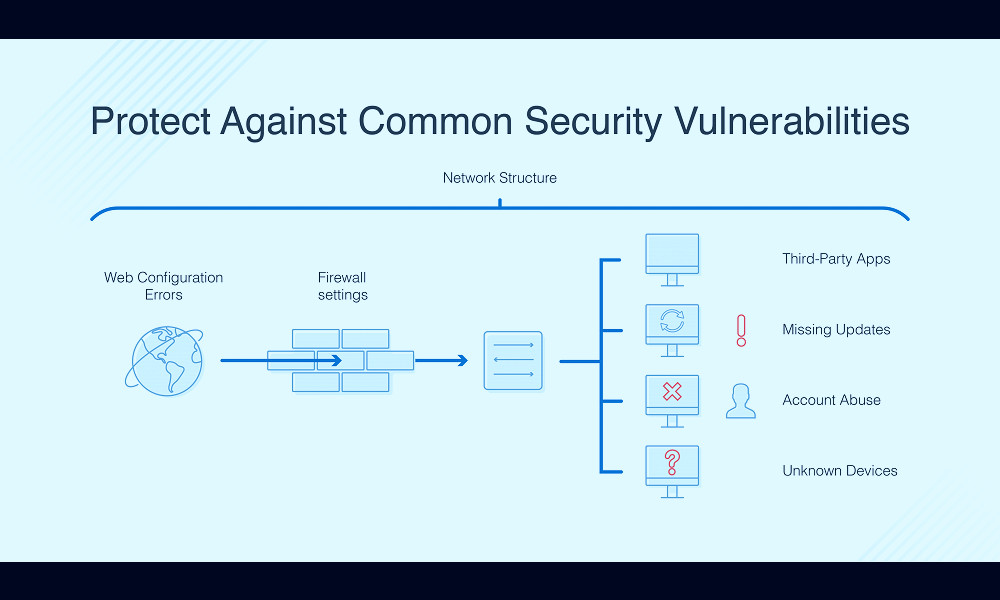
Vulnerability Management Tools are specialized software designed to identify, classify, prioritize, and help remediate potential points of exploitation in a network, known as vulnerabilities. These tools are essential for maintaining robust cybersecurity, aiding businesses in protecting their data and systems from potential cyber threats and breaches. They provide comprehensive risk assessment, patch management and continuous monitoring, making the complex task of vulnerability management efficient and manageable.
Overview of Vulnerability Management Tools
Vulnerability management tools are a critical component of any cybersecurity infrastructure. They help in identifying, prioritizing, and mitigating software vulnerabilities, thus enabling organizations to better protect their data and systems from cyber threats. Read more
Importance of Vulnerability Management
Vulnerability management is crucial for maintaining an organization's cybersecurity posture. By identifying potential vulnerabilities in an organization's software and systems, these tools help prevent unauthorized access, data breaches, and other cybersecurity incidents. Read more
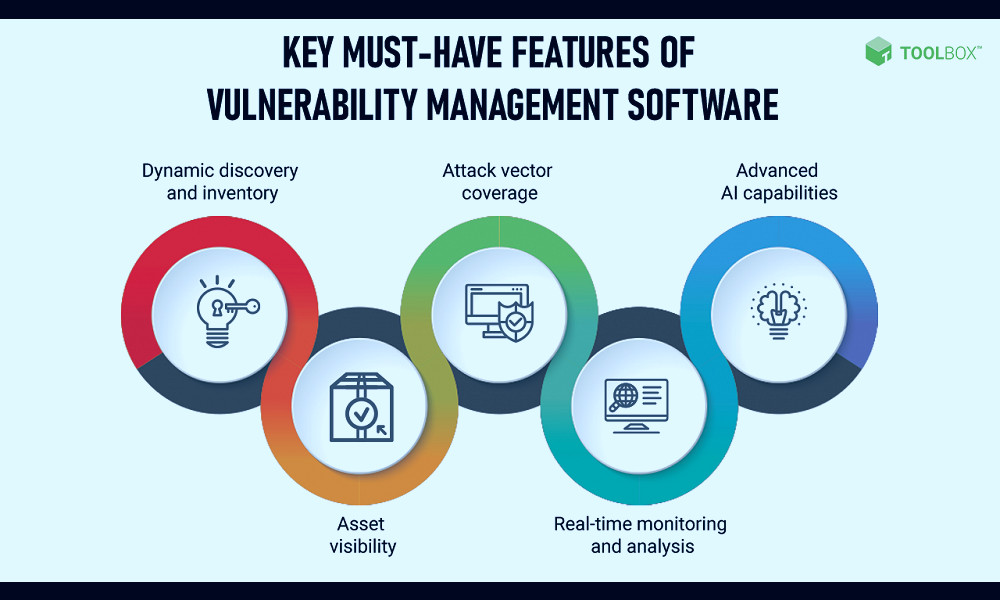
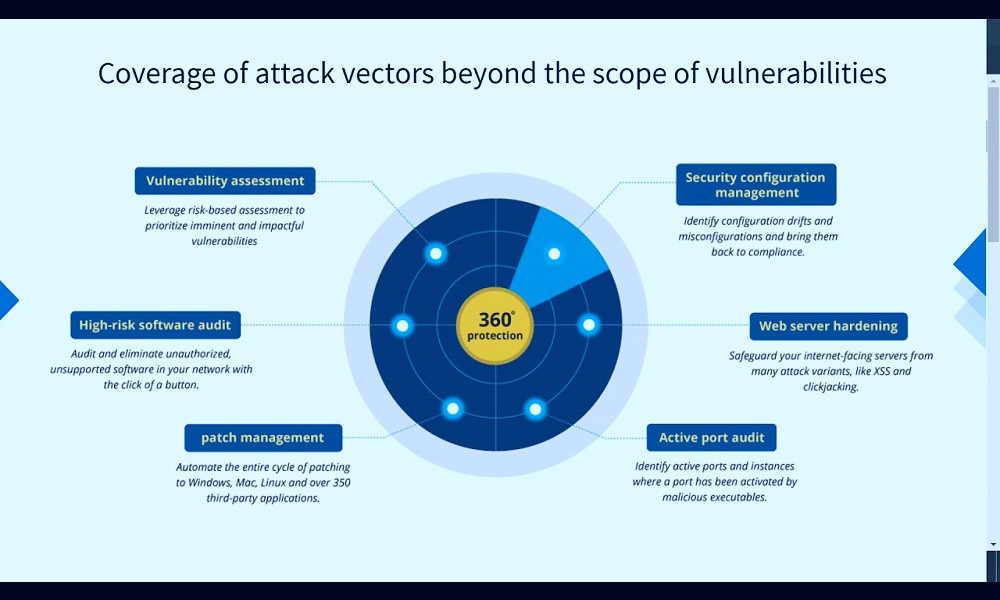
Key Features of Vulnerability Management Tools
Vulnerability management tools typically offer features like automated vulnerability scanning, vulnerability prioritization, patch management, and integration with other security tools. These tools also often include reporting and analytics capabilities to help organizations track and manage their vulnerability management efforts. Read more
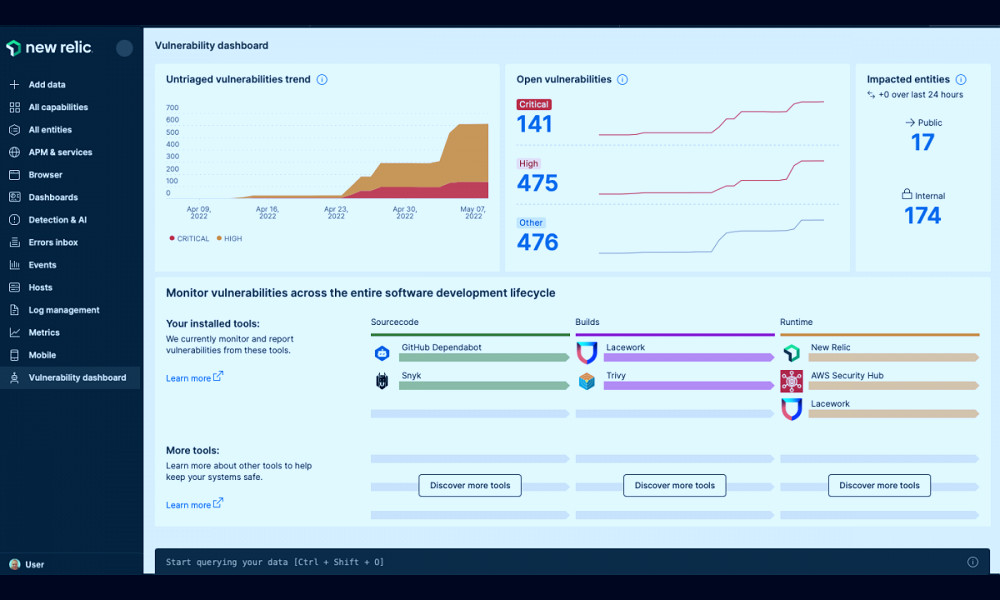
Vulnerability Scanning
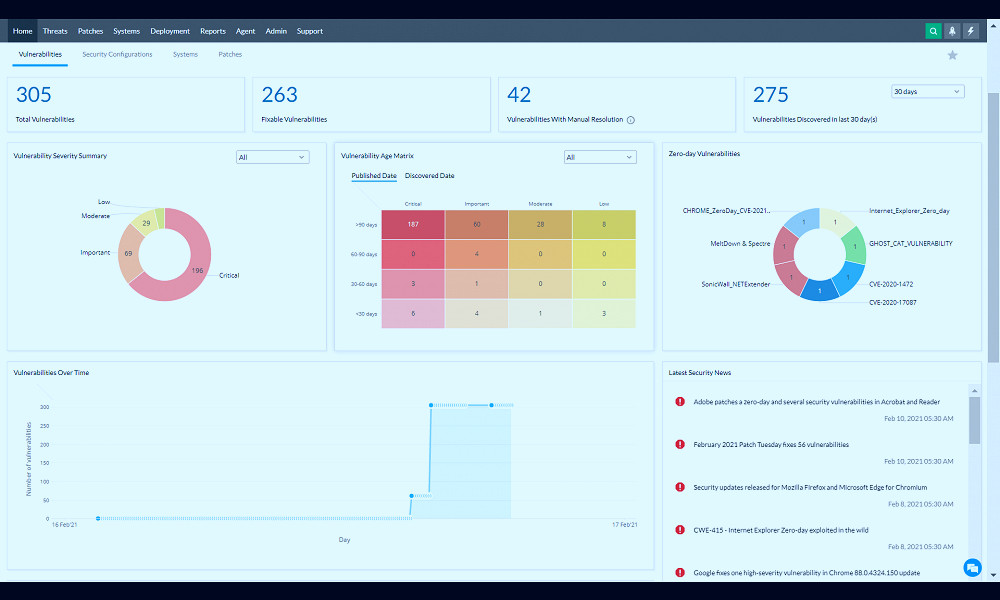
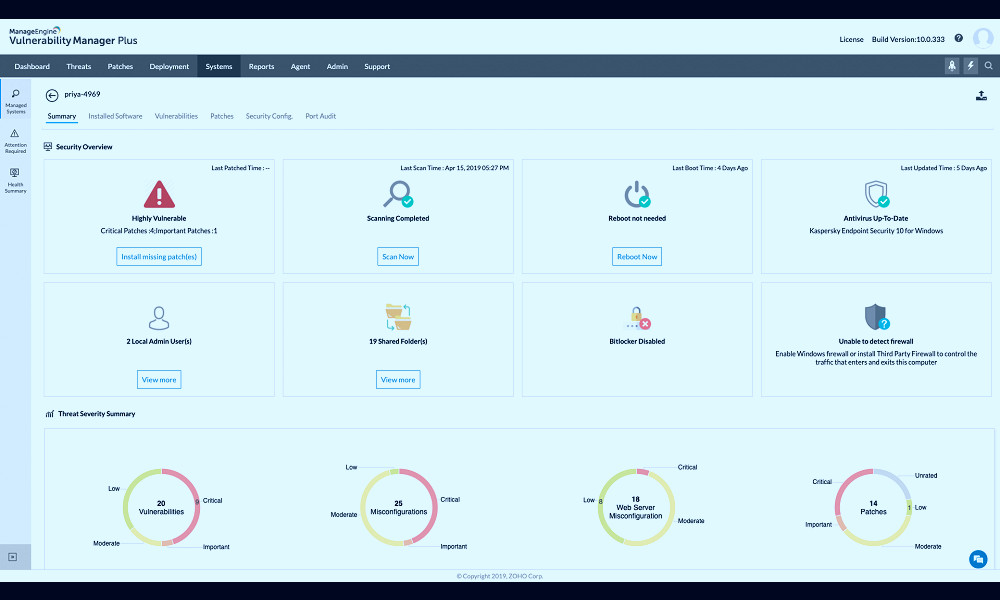
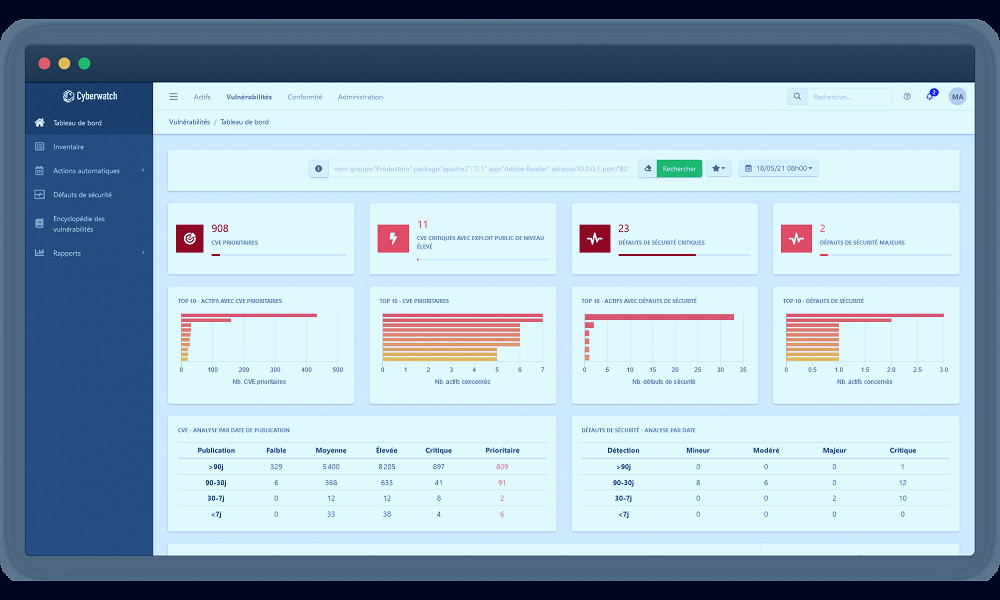
Vulnerability scanning, a core feature of vulnerability management tools, involves probing systems and software to identify potential vulnerabilities. This process can be automated to ensure continuous monitoring and immediate detection of new vulnerabilities. Read more

Vulnerability Prioritization
After identifying potential vulnerabilities, vulnerability management tools can also help organizations prioritize them based on factors like severity, ease of exploitation, and potential impact. This helps organizations focus their mitigation efforts on the most critical vulnerabilities. Read more
Patch Management
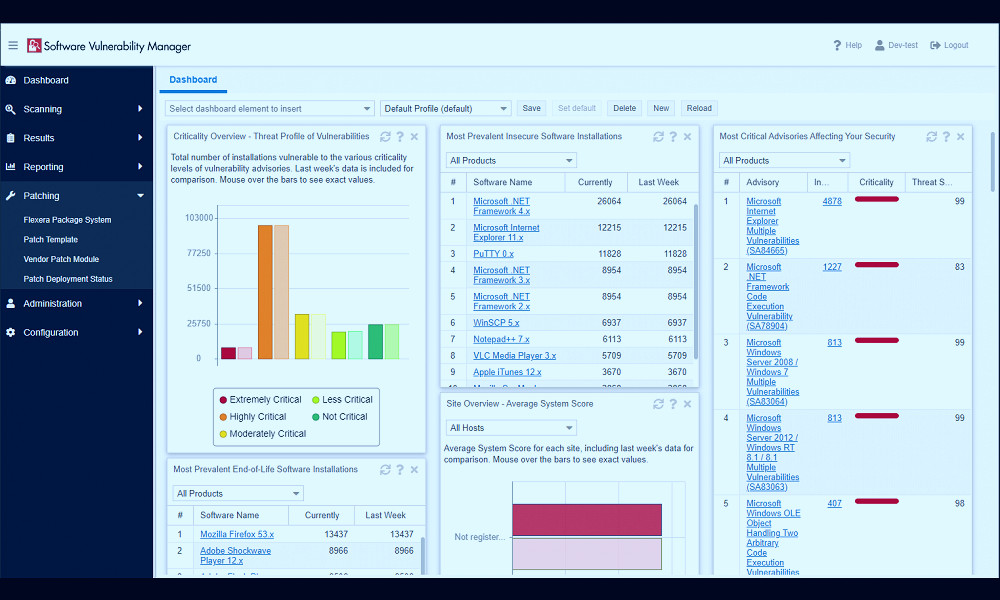
Patch management is another key aspect of vulnerability management. Vulnerability management tools often include capabilities to help organizations manage and apply patches to fix identified vulnerabilities, thus reducing their exposure to cyber threats. Read more
Integration with Other Security Tools
Vulnerability management tools often integrate with other security tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and endpoint protection platforms. This provides a more holistic view of an organization's security posture and enables more effective vulnerability management. Read more
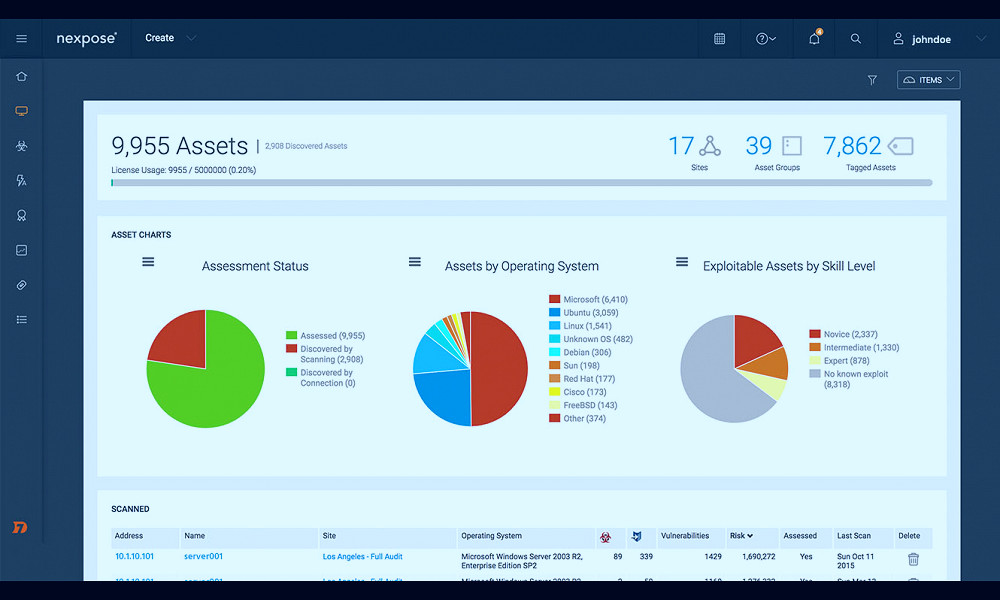
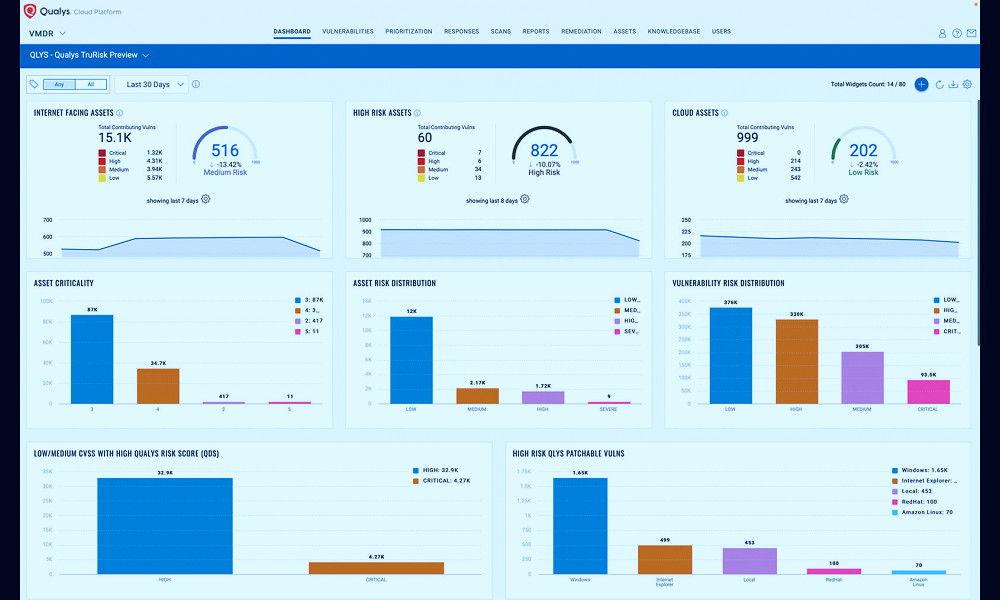
Reporting and Analytics
Vulnerability management tools also often include robust reporting and analytics capabilities. These can help organizations track the effectiveness of their vulnerability management efforts, identify trends, and make data-driven decisions to improve their cybersecurity posture. Read more

Leading Vulnerability Management Tools
Some of the leading vulnerability management tools in the market include Tenable Nessus, Qualys VM, Rapid7 InsightVM, and IBM QRadar Vulnerability Manager. These tools are recognized for their comprehensive feature sets, ease of use, and robust integrations with other security tools. Read more
Choosing the Right Vulnerability Management Tool
When choosing a vulnerability management tool, organizations should consider factors like the tool's feature set, ease of use, integration capabilities, and cost. They should also consider the tool's ability to scale and adapt to their changing security needs. Read more
Read more
 9 Best Vulnerability Management Tools in 2023 (Paid & Free)
9 Best Vulnerability Management Tools in 2023 (Paid & Free) 12 Top Vulnerability Management Tools for 2023 | eSecurityPlanet
12 Top Vulnerability Management Tools for 2023 | eSecurityPlanet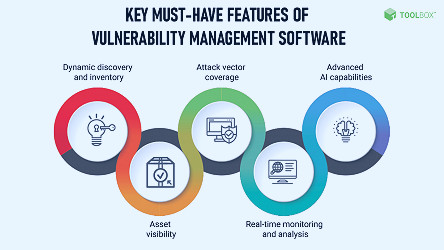 Top 10 Vulnerability Management Tools - Spiceworks
Top 10 Vulnerability Management Tools - Spiceworks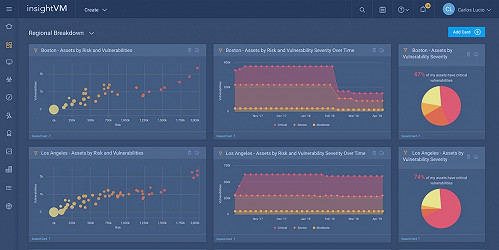 12 Top Vulnerability Management Tools for 2023 | eSecurityPlanet
12 Top Vulnerability Management Tools for 2023 | eSecurityPlanet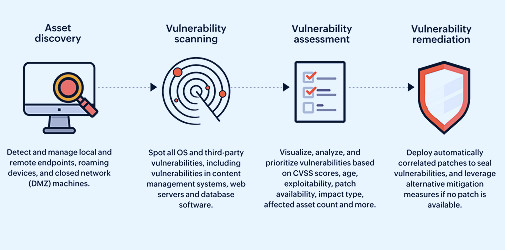 Vulnerability Assessment Tools & Checklists - ManageEngine Vulnerability Manager Plus
Vulnerability Assessment Tools & Checklists - ManageEngine Vulnerability Manager Plus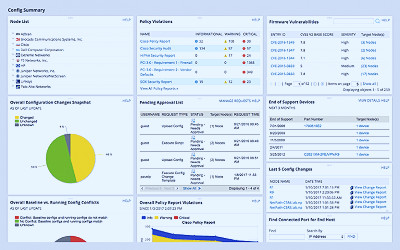 Top 10 Best Vulnerability Scanner Software | Tek-Tools
Top 10 Best Vulnerability Scanner Software | Tek-Tools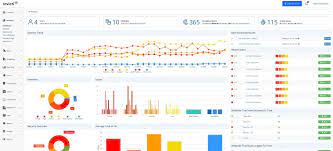 9 Best Vulnerability Management Tools in 2023 (Paid & Free)
9 Best Vulnerability Management Tools in 2023 (Paid & Free)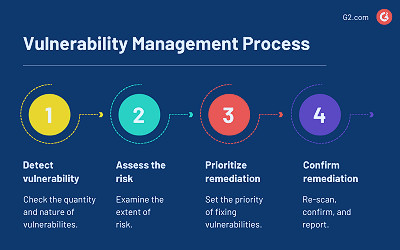 What Is Vulnerability Management? Get the Answers You Need
What Is Vulnerability Management? Get the Answers You Need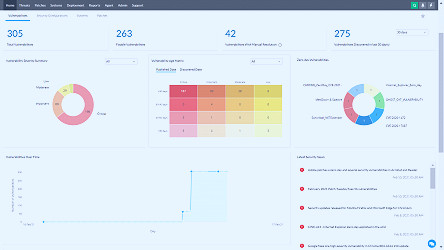 Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus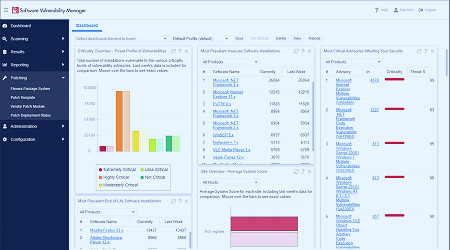 Software Vulnerability Management | Flexera
Software Vulnerability Management | Flexera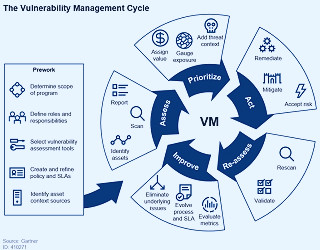 The New Vulnerability Management Guidance Framework
The New Vulnerability Management Guidance Framework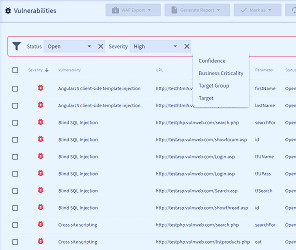 Vulnerability Management Software | Acunetix
Vulnerability Management Software | Acunetix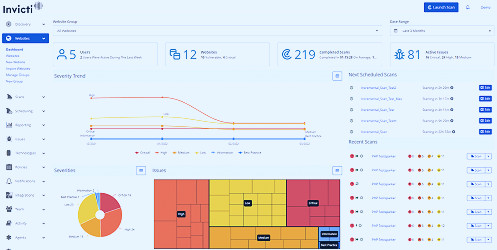 Best Vulnerability Management Tools for 2023
Best Vulnerability Management Tools for 2023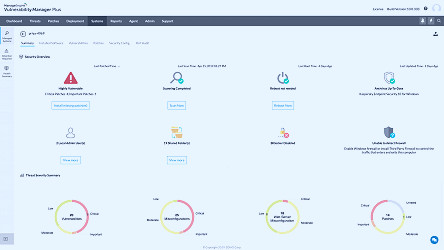 ManageEngine Vulnerability Manager Plus Software - 2023 Reviews, Pricing & Demo
ManageEngine Vulnerability Manager Plus Software - 2023 Reviews, Pricing & Demo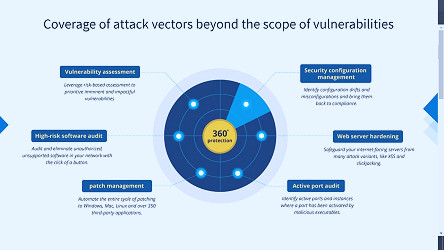 What is vulnerability management? | Vulnerability management process - ManageEngine Vulnerability Manager Plus
What is vulnerability management? | Vulnerability management process - ManageEngine Vulnerability Manager Plus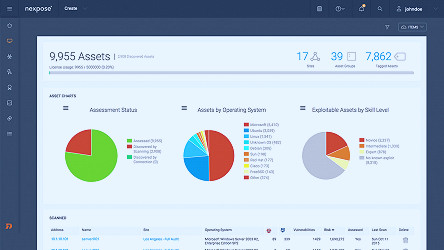 Nexpose On-Premise Vulnerability Scanner - Rapid7
Nexpose On-Premise Vulnerability Scanner - Rapid7 10 Best Vulnerability Management Tools - 2023
10 Best Vulnerability Management Tools - 2023 Know in Depth about Vulnerability Management Tools Market
Know in Depth about Vulnerability Management Tools Market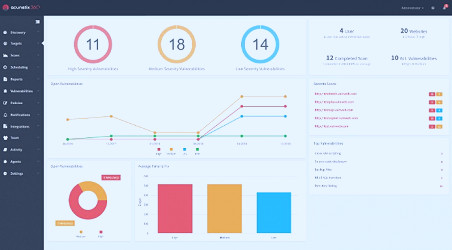 Top 15 Paid and Free Vulnerability Scanner Tools - DNSstuff
Top 15 Paid and Free Vulnerability Scanner Tools - DNSstuff Top 5 Best Vulnerability Management Software for 2022 - The Cybersecurity Times
Top 5 Best Vulnerability Management Software for 2022 - The Cybersecurity Times